Trezor Login and Multi-Sig Support | Securing Crypto with Trezor Login and Multisignature Access
Introduction to Trezor Login
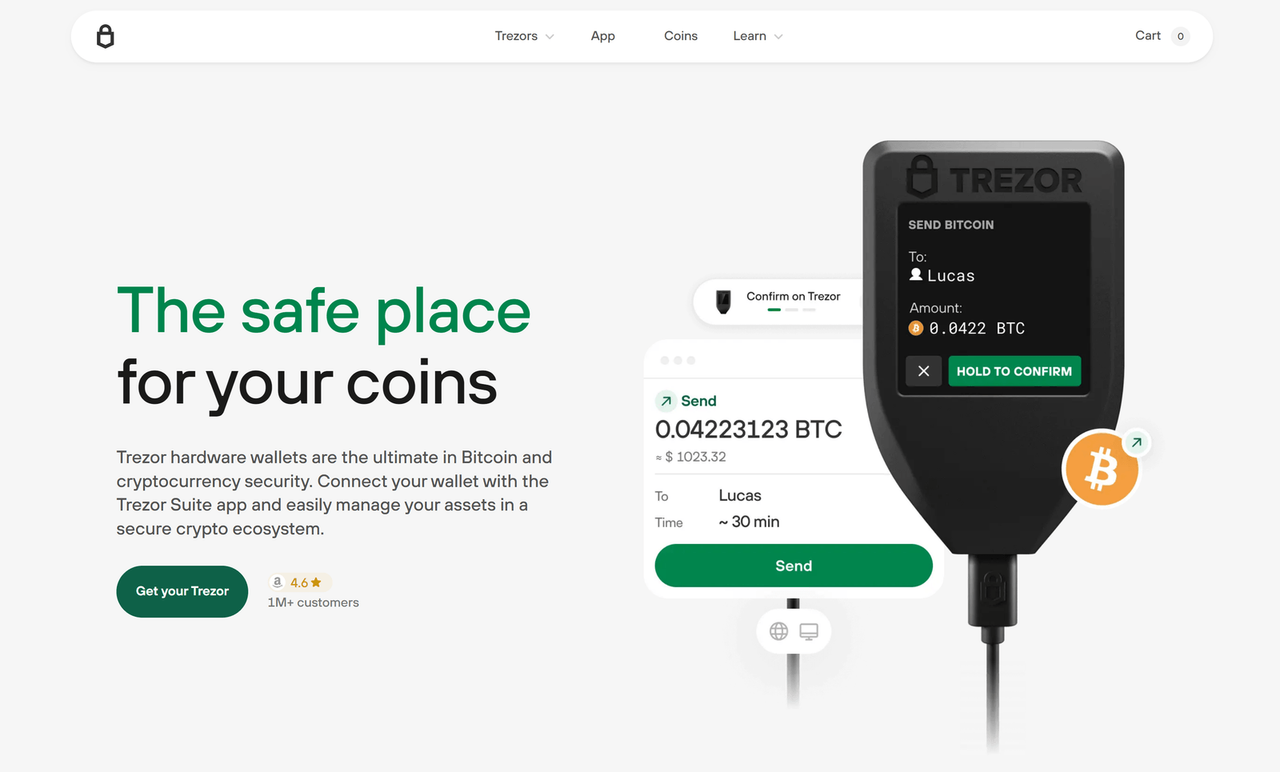
Trezor login is the essential security process that connects a user’s hardware wallet to supported platforms through the Trezor device. Whether accessing Trezor Suite, web3 wallets, or third-party services, Trezor login ensures private keys never leave the device. Trezor login offers a combination of usability and cryptographic protection, ensuring secure authentication even in environments prone to threats.
When using Trezor login, authentication happens by physically connecting the Trezor Model One or Trezor Model T, verifying the device’s identity, and confirming the login request manually. This process guarantees that credentials are never stored in browsers or vulnerable operating systems. Trezor login allows access to wallets and applications without exposing sensitive data, ensuring the user stays in control.
Conclusion: Trezor Login and Multi-Sig Are Stronger Together
Trezor login provides trusted, secure hardware access to the blockchain world. When paired with multi-signature wallet structures, it offers unmatched protection for digital assets. Whether you're an individual seeking peace of mind or an organization needing shared access, Trezor login combined with multi-sig architecture delivers layered security.
By using Trezor login in conjunction with trusted multi-sig platforms, users maintain full sovereignty, reduce single-point risk, and keep their crypto under the strongest protection available today.
Made in Typedream